Register as an organizer
Click the button below and finish your organizer registration, or fill out the form and we will be in touch to assist you.

When you're running a business, especially one that deals with a lot of customer information or relies heavily on its digital systems, you can't just wing it when it comes to security. Think of it like managing a busy store, you wouldn't just open the doors and hope for the best, right? You'd want to know your systems are solid, your inventory is secure, and nobody can just walk in and take things. That's where testing your security systems comes in, and it's not really something you can skip. It’s about making sure everything is locked down tight before someone else finds a way in. This is especially true for things like Box Office Management systems, where customer data and financial transactions are happening all the time.
Penetration testing, sometimes called ethical hacking, is basically a way to find weak spots in your digital defenses before the bad guys do. It’s like hiring someone to try and break into your house to see if your locks and alarms actually work. It’s not just about running automated scans; it’s about thinking like a real attacker.
At its heart, penetration testing is a simulated cyberattack. Security pros try to find and exploit vulnerabilities in your systems, networks, or applications. The goal is to see what an attacker could do and how much damage they could cause. This proactive approach helps organizations fix problems before they become major security breaches. It’s a way to test your security policies and controls to see if they’re really doing their job.
Penetration tests can be done in a few different ways, mostly depending on how much information the testers have beforehand. This really changes how the test plays out:
The way a test is set up can really change what you find. Knowing how much information to give the testers is a big part of planning a successful test.
Automated security scans are useful, sure, but they often miss the subtle stuff. Think of it like this: a scanner might tell you a door is unlocked, but a penetration tester will try to pick the lock, jimmy the window, or even see if they can bluff their way past a guard. They find flaws in how things are configured, custom software, or even just overlooked network paths that automated tools just don't catch. This kind of testing helps you figure out what’s really at risk and where you should focus your efforts first. It’s about understanding the potential impact of a real attack, not just ticking a box. You can find out more about the methodology of penetration testing to get a better idea.
When we talk about testing your digital defenses from the outside, black box testing is the way to go. Think of it like trying to get into a building without knowing anything about its layout or security systems, you’re just using what you can see from the street. This approach is all about mimicking how a real attacker, someone with no inside information, would try to find weaknesses in your external setup. It’s a pretty straightforward way to see how your firewalls, public facing websites, and other exposed services hold up when someone’s actively trying to poke holes in them.
This method really puts you in the shoes of an outsider. Testers don’t get any internal blueprints, source code, or system details. They have to rely on publicly available information, network scanning tools, and a good dose of creativity to map out your digital perimeter. It’s about finding those entry points that an external threat actor might discover. This realistic simulation is key to understanding how your defenses truly perform against an unknown adversary. It’s a bit like trying to solve a puzzle with only the pieces you can see on the box lid. For a good overview of how this works, you can check out black box penetration testing.
Part of what makes black box testing effective is dynamic analysis. This means testers are actively interacting with your live systems and applications. They’re not just looking at code, they’re observing how the system behaves in real time. This helps uncover issues that only show up when the software is running, like problems with how data is handled during a transaction or how the system responds to unexpected inputs. It’s about seeing the system in action, not just on paper.
There are several good reasons to use this approach:
Black box testing is particularly useful for assessing how well your organization can detect and react to unexpected probes or attacks from the outside. It’s a practical way to gauge the strength of your external security posture without needing to share internal secrets, making it a good choice for vendor assessments or initial security checks. The setup is usually quicker, and it’s less intrusive than methods requiring deep internal access. It’s a solid way to get a handle on your exposed digital footprint.
White box testing isn’t just about finding bugs, it’s about truly understanding how your system behaves under the hood. By looking at the internal structure, code paths, and logic, testers can uncover hidden issues that black box testing might miss. This approach gives developers and QA teams deep insights into performance, security, and edge cases, helping ensure that every function does exactly what it’s supposed to do.
White box testing, sometimes called clear box or glass box testing, is where testers get the full picture. We're talking source code, network maps, system configurations, the whole shebang. It’s like giving a mechanic the car’s blueprints and all the tools before they start looking for problems. This means testers don't waste time trying to figure out how things work, they can jump right into analyzing the inner workings. They look for things like:
This method is perfect for finding those really hidden vulnerabilities, the ones an outsider wouldn't even know to look for. It’s a deep dive, plain and simple.
With all the information from white box testing, we can do more than just find bugs. We can actually figure out how bad they are. Testers assess the potential impact on things like data privacy, system integrity, and availability. Then, they rank these vulnerabilities based on how likely they are to be exploited and how much damage they could cause. This context is super helpful for decision makers. It means they can focus on fixing the biggest threats first, instead of getting bogged down with minor issues.
Here’s a quick look at how we might rank a vulnerability:
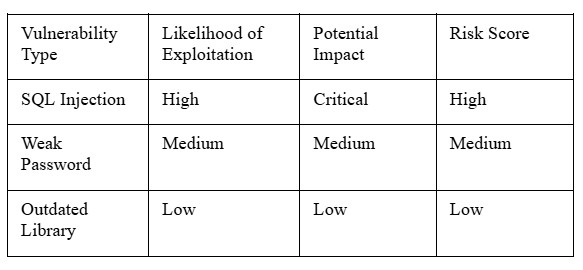
This detailed analysis helps organizations make informed decisions about where to put their security resources, making the whole process much more efficient.
If you’re really serious about making your software and systems tough to break, white box testing isn't just a nice to have, it's pretty much required. It gives you an inside look, like an X-ray for your digital assets. This approach helps catch those sneaky attacks that might slip past tests that only look at the outside. It’s about understanding what’s happening under the hood so you can fix problems before bad actors find them. While it takes time and resources, the clarity it provides on your security posture is hard to beat.

Choosing the right penetration testing strategy really depends on what you're trying to find and what your goals are. It's not a one-size-fits-all situation, and picking the wrong approach can mean you miss important security holes.
Black box testing is your go-to when you want to see how your defenses look from the outside, just like a real attacker would. Think of it as testing your perimeter. It's particularly useful for:
This method is great for simulating external threats and understanding your readiness against attackers who have no prior knowledge of your systems. It gives you a realistic view of your external security posture. You can find out more about these kinds of tests in this guide penetration testing methodologies.
White box testing is the way to go when you need to really dig deep and understand your system's internal workings. It's like giving a security expert the keys to the castle and asking them to find every single flaw. You'd typically choose this for:
This approach is fantastic for uncovering vulnerabilities that might be hidden from external view, things that automated scans often miss. It provides a much more detailed look at your internal risks.
Deciding between black box, white box, or even a mix of both involves looking at a few things:
Ultimately, the goal is to get the most useful information for improving your security. Sometimes, a quick external check is enough. Other times, you need to go deep inside the code. Understanding these differences helps you make a smarter choice about where to focus your security efforts and budget.

Even with the best intentions, penetration testing isn't a magic bullet. Both black box and white box approaches have their own sets of challenges and potential downsides that you really need to be aware of. Ignoring these can lead to a false sense of security or wasted effort.
With black box testing, the biggest hurdle is that testers are working blind, sort of. They don't get to peek under the hood, meaning they might miss vulnerabilities that are hidden deep within the code or internal network architecture. It's like trying to find a leaky pipe without knowing where the pipes even are. If the testers don't stumble upon any obvious flaws from the outside, it's easy to think everything is fine, but that's not always the case. There's a real risk of overlooking serious issues just because they weren't visible from the external attack surface. The time it takes can also be unpredictable, some tests are quick if there are easy wins, while others can drag on for weeks if the system is complex. This variability means clear communication about timelines and what's actually achievable is super important.
When conducting black box tests, it's vital to establish clear rules of engagement. This prevents accidental disruption to live operations or the exposure of sensitive data. Agreeing on the scope, boundaries, and fail-safe mechanisms beforehand is key to avoiding unintended consequences and staying on the right side of legal and ethical lines.
White box testing, while thorough, isn't without its own set of problems. For starters, it requires a significant investment of time, skilled personnel, and access to sensitive internal information. This can get pretty expensive, pretty fast. Because testers have all the information, there's also a risk of 'tunnel vision', they might focus too much on known weak spots and miss entirely new or unexpected attack vectors. Think of it like a mechanic who only knows how to fix one specific type of engine problem; they might overlook a completely different issue. The sheer volume of data generated can also be overwhelming, making it tough to sort through the noise and pinpoint the real threats. Having a solid plan for triaging and reporting findings is absolutely necessary to avoid getting bogged down.
Here's a quick look at some common issues found with white box testing:
No matter which method you choose, ethical and operational considerations are paramount. Sharing sensitive internal data for white box testing requires a high degree of trust and robust confidentiality agreements. It's often best to conduct these tests in staging or separate test environments rather than on live production systems to avoid any risk of crashes or data leaks. For black box testing, the focus is on simulating real world attacks without causing harm. This means defining the scope very carefully and having backup plans in case something goes wrong. It's about being thorough without being destructive. For organizations using third-party services, like ticketing systems from companies such as Spektrix, understanding how they handle security testing is also part of the bigger picture. Ensuring that any testing aligns with business goals and compliance requirements is always the main objective, and it's something that needs careful planning. The choice between black box and white box testing often comes down to factors like budget, the sensitivity of the data you're protecting, and your overall risk tolerance. For instance, if you're developing new software, catching security bugs early with white box testing is often the most sensible approach.
You know, sometimes you just gotta combine things to get the best results. It’s like making a sandwich – you can’t just have bread, right? You need some filling, maybe some sauce. Cybersecurity is kinda the same way. Relying on just one type of testing, like only looking at things from the outside (black box) or only from the inside (white box), can leave you with blind spots. That’s where a hybrid approach really shines.
Think about it. Black box testing is great for seeing how your defenses look to someone who knows nothing about your systems. It’s like checking if your front door is locked and the windows are shut when you’re not home. But it won’t tell you if someone’s already hidden in the closet. White box testing, on the other hand, gives you that full inside look. It’s like checking every room, every closet, and under every bed. Combining them means you get both the outside view and the inside scoop. This layered strategy gives you a much clearer picture of your overall security. It’s about covering all the bases, from the obvious external threats to the sneaky internal ones that might be missed otherwise.
When you start with black box testing, you’re basically putting on an attacker’s hat. You’re looking at your systems from the internet, using only what you can find publicly. This helps you see how strong your outer walls are and how well your security team can spot and react to an unknown attacker. It’s all about testing your perimeter and your response capabilities in a real-world scenario. You’re not getting any special information, just trying to break in like a regular hacker would. This kind of testing is super useful for finding those common vulnerabilities that attackers often go after first.
Now, white box testing is where you open up the system’s blueprints. You give testers full access to the code, the architecture, and how everything is configured. This lets them dig deep and find those more complex or hidden issues that black box testing might miss. It’s really important for making sure new software is secure before it even goes live, or for checking compliance with certain rules. By integrating this deep dive into your development process, you can catch and fix problems early on, which is way cheaper and easier than fixing them after something goes wrong. It’s about building security in from the ground up, not just patching it on later.
Look, whether you're testing from the outside like a curious neighbor or from the inside with all the keys, the main point is this, you gotta test. Ignoring potential security holes is like leaving your front door wide open and hoping for the best. It just doesn't work in the long run. Both black box and white box methods have their place, and often, using both gives you the clearest picture. So, get those systems checked out before something bad happens. It’s really that simple.
Think of penetration testing like a security check-up for your computer systems. It's like hiring a good guy hacker to try and break into your stuff to find weak spots before the bad guys do. This helps you fix problems before they cause real damage.
Black box testing is like trying to get into a locked house without knowing anything about it. The testers only know what an outsider would see. This helps find problems with your outer defenses, like how strong your doors and windows are.
White box testing is like having the keys to the house and knowing all the secret passages. Testers get to see all the inner workings, like the computer code. This helps find deeper, hidden problems that someone from the outside wouldn't find.
Usually, it's best to use both! Black box testing checks your outside defenses like a real attacker would. White box testing then goes deep inside to find hidden issues. Using both gives you the most complete security picture.
Sometimes, black box testing might miss problems hidden deep inside the system because testers don't have access to the inside. Also, if they don't find any issues, you might think you're safe when you're not.
White box testing can be expensive because it takes a lot of time and skilled people. Also, since testers have all the information, they might focus too much on known weak spots and miss brand new ways attackers might try to get in.
More blogs
Click the button below and finish your organizer registration, or fill out the form and we will be in touch to assist you.